Written by Dr. Sabah Suhail
Securing Cyber-Physical Systems (CPSs)
The convergence of information technology (IT) and operational technology (OT) systems in cyber-physical systems (CPSs) enables interconnected and autonomous operations. However, this integration also introduces new attack vectors, posing significant risks to social, economic, and business sectors. Securing CPSs requires evaluating system functionality and security without disrupting ongoing operations. There are several existing solutions designed to secure systems, such as intrusion detection systems. These systems detect malicious activities by identifying deviations or abnormal patterns from established benign behaviour. However, setting up and maintaining such systems can be both time-consuming and costly, cannot replicate or reconfigure scenarios for future investigations, and may not address the entire system lifecycle.
The question is:
“How to secure CPSs?”
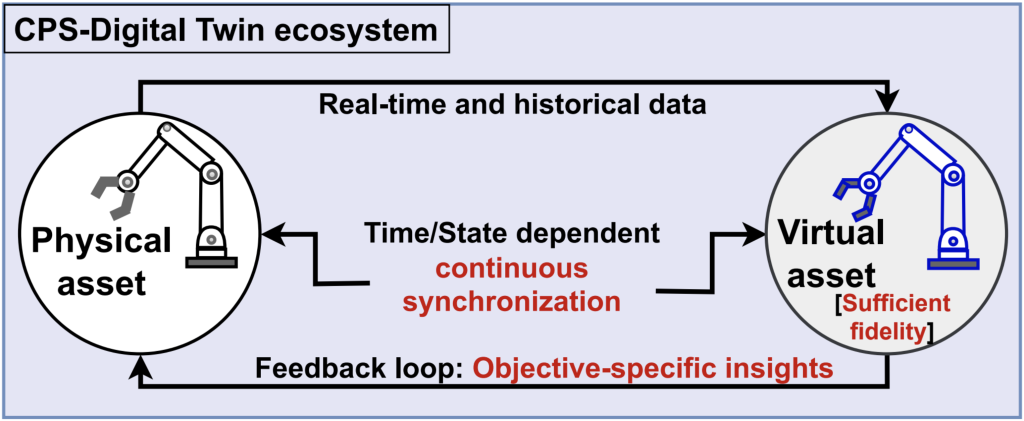
Digital Twins
One of the promising solutions to secure CPSs is digital twins (DTs). DTs are virtual replicas of their physical counterparts that must:
- exhibits sufficient fidelity in terms of attributes and services
- maintains a continuous (time/state-dependent) synchronised feedback loop
- provides objective-specific actionable insights such as assessments, predictions, optimisation, and calibration-related information while covering the entire system lifecycle.
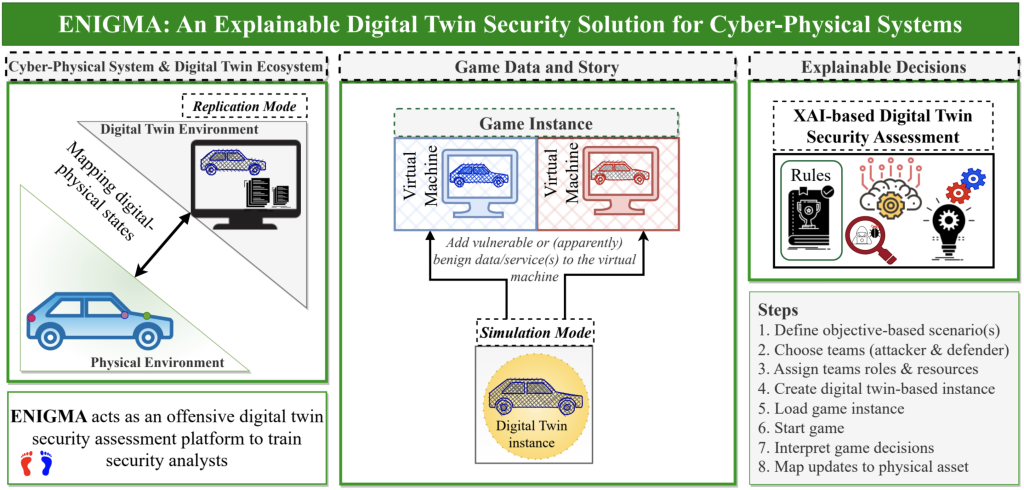
DTs as a testing and training platform
In (sEcuriNg dIgital twins through GaMification Approach) (ENIGMA), we use DTs as a gamification platform, leveraging them for offensive security simulations involving direct attacks on DT instances.
Research objectives
The objective of this research is to:
- Training: Provide security analysts with a training environment where attack scenarios can be simulated in a controlled, interactive setting, enhancing their readiness for real-world threats.
- Testing: Assess system security without negatively affecting ongoing operations.
- Evaluation: Use explainable AI to evaluate gaming outcomes, supporting justifiable reasoning on the formulation of specific cybersecurity defenses in a gaming context.
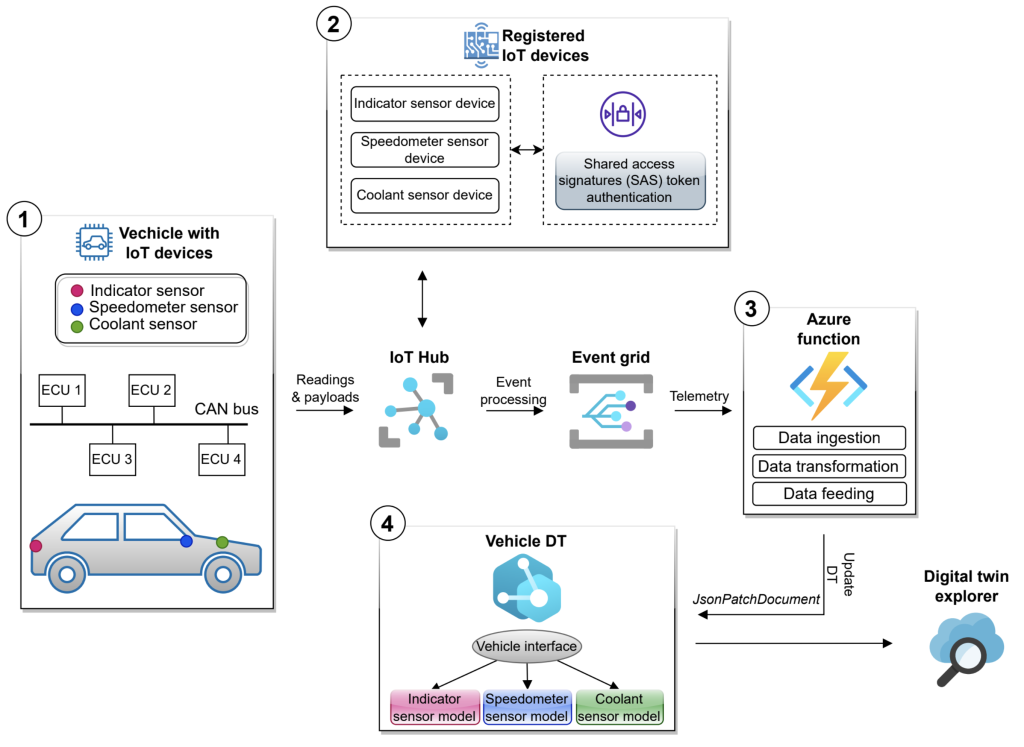
Building a DT
We chose the Microsoft Azure Digital Twin (ADT) platform for a vehicle use case to gamify in-vehicle network traffic.
- Configure ECUs and sensors – The process starts with configuring the vehicle’s electronic control unit (ECUs) and communicating with the CAN bus. Three sensors, including a speedometer, indicator, and coolant, are installed on the respective ECUs to emit data to the vehicle DT.
- Register and authenticate sensors – The sensor devices are registered on the Azure IoT Hub and authenticated using Shared Access Signatures (SAS) token authentication.
- Route data to vehicle DT – The Azure IoT Hub receives sensor data via the CAN bus. Event Grid routes the data to the vehicle DT through an Azure function, which handles data ingestion, transformation, and feeding to the DT.
- Transform data and update DT – The Azure function transforms the data into JSON format using JsonPatchDocument, making it readable by the vehicle DT. This information updates the vehicle DT, which can be visualised and interacted with via Azure Digital Twin Explorer.
Resources

Catch-up on the Gemini Calls by Sabah Suhail
Contact
Email: s.suhail@qub.ac.uk



Leave a comment